- 5 Minutes to read
- Print
- DarkLight
- PDF
Configuring Security Options
- 5 Minutes to read
- Print
- DarkLight
- PDF
Security Options refer to settings or configurations that control access, permissions, and security-related aspects for users within those groups.
Is the shield icon the Security Configurations icon?
Yes. Click the Shield icon to view the list of Security Configurations options.
First, let's understand the Status Indicators of the security (shield) icon to assess the level of configurations for each user or user group.
Navigate to Maintenance > Administration > User & Role Management.
Click the User or User Group tab.
You can start configuring these settings by selecting the security options (shield) icon in two ways:
Select the created user or the user group and click directly on the security options (shield) icon within the Security column.
.png)
Notes:
When you hover over the security options icon, you can interpret the status as follows:
No color: Indicates that no access has been configured
Red: Indicates that the access has been configured for a few areas
Green: Indicates that the access has been configured for all areas
Once the user or user group is created, the configurations are not done, so the default color and status is "no color".
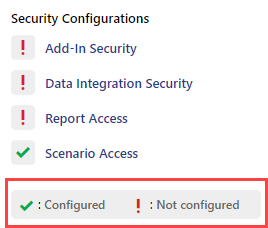
Additionally, when you click the security options icon, you can determine the configuration status of each area by the associated indicators. There are two statuses: Configured and Not configured. A green checkmark indicates that the configuration is complete, while the other indicator suggests that other areas are yet to be configured.
Select the user or the user group and click the Security Options (shield) icon in the header.
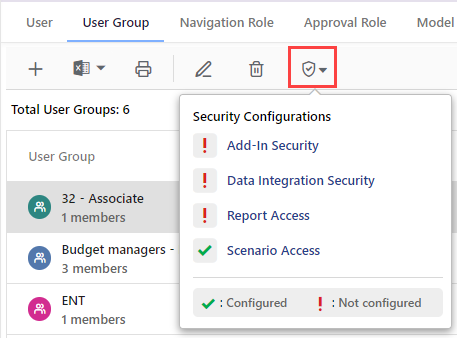
Using this option, you can configure the following areas:
Add-In Security
Setting up add-in security is important when using Planful Offline Planning, which is an Excel planning tool that allows you to download and perform budgeting tasks while not connected to the application.
Note:
This is optional and you need to complete this only if you use Planful Offline planning.
To learn how to set up add-in security, click here.
To learn more about offline Planning, click here.
Approval Role Setup
Approval roles are used in the Planning module to specify the actions users can perform during the budgeting process. For example, you can assign a budget manager with an approval role. Given this role, the budget manager can approve budgets.
Approval roles may have varying levels of user responsibility for budget entities. For example, when a user has access to two entities (A and B), but has HR responsibility for entity B only, the user can be restricted to view only specific data based on HR access for the approval role assigned for the entity.
To learn how to set up the Approval Role, click here.
Consolidation Security
The Consolidation Security is used to set security for Centralized and Decentralized users. A centralized user has access to all company members in a scenario. A decentralized user has access to specific dimension members only. The Company/Legal Entity Member Selector distinguishes between Centralized and Decentralized Consolidations. If you are at the root member (defined as the top member in the hierarchy), then you are interacting as a Centralized user managing the Consolidation Process in its entirety. If you have been provided specific member access within the hierarchy and you select a Company from the member selector, then you are interacting in Decentralized mode. This means that the modules available may be restricted and you may have limited access to Company intersections for modifying data.
To learn how to set up Consolidation Security from the User & Role Management, click here.
Data Integration Security
Data integration security is comprised primarily of Data Load Rules. A Data Load Rule tells the system how to handle data values in the data source during a data load.
You can assign users and user groups with data integration security options, which allows users and user groups to access specific Data Load Rule (DLR) processes. You can create data load rules to load files, copy and paste data, and use web services to load segment hierarchies, attributes, attribute hierarchies, entity hierarchies, users, HR data, currency exchange rates, and other data.
To learn how to set up Data Integration Security, click here.
Dimension Security
Secure dimension members (financial segments) based on reporting area and activate security for one or more dimensions.
To learn how to set up Dimension Security from User & Role Management, click here.
Report Access
To provide users and user groups with access to generated reports, each user or user group must be assigned access privileges. Any user with access to User & Role Management can update Report Access for a user, user group, or artifact.
To learn about how to configure Report access, click here.
Scenario Access
To provide users and user groups access to a scenario, each user or user group must be assigned access privileges.
The user will only have access to the selected scenarios and members for Reporting purposes. For example, when a user runs a report that includes a scenario the user doesn’t have access to, that scenario will not be available in the report. Similarly, if a user has permission to view a scenario when a report was created and later the permissions are revoked, the report is run for only those scenarios on which the user currently has permissions. Data will not be displayed for the scenarios for which permissions are revoked.
Note:
The Actual scenario is not subject to security and is available to all the users.
To learn how to assign a scenario access to a user or user group, click here.
Workforce Reporting Access
By default, users gain access to Finance and Workforce reports based on their Dimension and Budget Entity Security settings.
The Workforce Reporting Access feature allows administrators to restrict specific users from viewing Workforce data, ensuring only authorized users can view them.
Note:
This is an opt-in feature. Contact the Planful Support team to enable the Workforce Reporting Access feature.
Once the feature is enabled, administrators can grant users permission to view the workforce data when running reports. The reports still inherit security settings from Dimension Security and Budget Entity Security.
Note:
Users without permission can still view the reports but cannot view the data within them when running reports.
To learn how to provide access to Workforce Reporting when the Workforce Reporting Access feature is enabled, click here.
Dimension and Budget Entity Security
Workforce Reporting enables structured, ad hoc analysis of workforce planning dimensions and measures. Workforce Reporting is integrated into the application as a Reporting Area, allowing you to report on employee-specific compensation and other financial dimensions.
To learn about Securing Reports and Data, click here.

